- Personal
- Membership
- Membership
- Rates & Fees
- Checking
- Checking
- Personal Loans
- Personal Loans
- Wealth Management
- Investment Services
- Financial Advisors
- Resource Center
- Business
September 22, 2020
Recognizing and Avoiding Scams

Scammers are becoming more sophisticated in their tactics to exploit people. From phishing schemes to investment frauds, it’s hard to navigate the landscape of potential scams. Understanding the red flags and staying vigilant are crucial steps to safeguarding yourself from falling prey to scams in the digital age.
Malware
Malware is malicious software that can infiltrate computer networks, steal sensitive information, and disrupt your device’s normal operations. Common examples include:
- Viruses: code that replicates itself by modifying other computer programs and inserting its code.
- Ransomware: encrypts files and demands payment for their release, often causing financial losses and operational disruptions.
- Worms: replicates itself to spread to other computers, often without any user interaction.
- Trojans: misleads users of its true intent, often disguised as legitimate software, to gain unauthorized access to a computer.
You can get malware by clicking on certain links or downloading seemingly harmless things to your computer. These links can appear in ads, social media posts, emails, pop-up windows, or even messages from hacked accounts of friends or family. You can spot a potentially dangerous link by looking for things that offer services that are too good to be true or have urgent messaging.
Be cautious when clicking on links sent to you without prior permission, especially if the language is generic or doesn’t sound like the sender. If you click on a link and suspect your device is compromised, immediately run a scan using antivirus software and take any necessary actions as suggested by the software. Stay vigilant and avoid clicking on suspicious links to keep your device and personal information safe.
Phishing Scams
Phishing scams are fraudulent attempts to deceive people into revealing sensitive information. Phishing uses fake emails, messages, or websites that appear to be from trustworthy sources. Phishing scams use sophisticated tactics like creating convincing replicas of legitimate websites, exploiting fear or curiosity, and using deceptive urgency. These tactics can lead individuals to disclose sensitive information or click on malicious links without thinking it through.
You can significantly reduce the risk of falling victim to phishing scams by:
- Being skeptical of unexpected emails or messages
- Verifying the sender’s authenticity
- Using multi-factor authentication
- Staying informed about common phishing tactics
Impersonation Scams
Impersonation scams involve scammers pretending to be someone else to deceive individuals for financial gain or personal information. Scammers pose as trusted entities and manipulate victims into divulging sensitive information or transferring funds. To avoid these deceptive tactics, verify the identity of anyone making unsolicited contact and refrain from sharing personal or financial details without thorough authentication.
One common impersonation scam is the scammer posing as the IRS, calling you, and demanding money. The IRS will never call to ask for payment. If you receive a call from someone claiming to be from the IRS, hang up immediately. The IRS will only contact you through mail or in-person interview.
Regarding debt collection, it’s important to be cautious. You can research the collector and ask them to send a Debt Validation Letter to confirm the debt’s validity. This coach can help you with the process.
“Pig Butchering” Scams
“Pig butchering” scams are a form of investment fraud that often begins with unsolicited messages on social media or dating apps. These scams are becoming increasingly common since they allow scammers to quickly build a false sense of trust and emotional connection with their victims over time. Eventually, scammers introduce a “can’t miss” investment opportunity, typically involving cryptocurrency.
To appear legitimate, scammers may even direct their victim to fake websites, apps, or platforms that show impressive—but false—”profits” to further entice the victim to invest larger sums. Once the victim invests significant funds, the scammer disappears with the victim’s money, leaving them financially and emotionally devastated. The term “pig butchering” refers to the scammer “fattening up” the victim with attention and false promises before ultimately defrauding them.
How to Avoid “Pig Butchering” Scams
Reduce your risk of falling victim to a “pig butchering” scam by following these safe online habits:
- Be cautious of unsolicited messages or fast-forming online relationships: Especially those that quickly turn personal or romantic and/or evolve into investment or financial discussion.
- Avoid investment advice from online acquaintances: Never invest based on recommendations from someone you’ve only met online, especially if there is a promise of unrealistic returns.
- Research investment opportunities independently: Always conduct thorough independent research and consult with trusted financial advisors before making any investment decisions. Verify the legitimacy of any platform or opportunity through trusted financial advisors or official sources.
- Be wary of high-pressure tactics: Scammers often create a sense of urgency to prompt quick decisions. Remember, genuine investment opportunities are rarely found through unsolicited online interactions.
Tech Support Scams
Tech support scams involve fraudsters posing as technical support representatives from well-known companies. They often contact victims via phone calls, pop-up messages, or unsolicited emails, claiming that the victim’s device has a virus or some other critical issue. These scammers then urge the victim to grant remote access to their personal computer or even pay for unnecessary services. Once a scammer gets access to the computer, they can steal personal information (credit card numbers, social security numbers, etc.).
How to Avoid Tech Support Scams
- Don’t trust unsolicited tech support contacts: Remember, legitimate companies won’t proactively contact you out of the blue to fix your computer.
- Avoid clicking on suspicious pop-ups or links: If you receive an unsolicited call or see a suspicious pop-up, do not click on any links, provide any personal information, or grant remote access to your device.
- Never grant remote access to unknown individuals: Only allow access to trusted professionals you’ve contacted directly.
- Verify issues through official channels: If you are concerned about a potential issue with your computer, independently contact the official support channel of the company in question through their verified website or phone number.
Government Imposter Scams
Government imposter scams involve individuals falsely claiming to represent government agencies such as the Internal Revenue Service (IRS), Social Security Administration (SSA), or local law enforcement. These scammers often use intimidation tactics, claiming that the victim owes money, has missed a court date, or is facing legal action. They may demand immediate payment, often through unconventional methods like wire transfers, gift cards, or cryptocurrency, and will threaten arrest or other severe consequences if the victim doesn’t comply. They may also try to solicit personal information like Social Security numbers or bank account details.
How to Avoid Government Imposter Scams
- Know official communication methods: Government agencies typically initiate contact through official mail, not phone calls or emails. If you receive a suspicious call or email from someone claiming to be a government official, do not provide any personal information or payment.
- Be skeptical of urgent payment demands: Especially those requiring unconventional payment methods. Legitimate government agencies will never demand immediate payment over the phone or through methods like gift cards or cryptocurrency.
- Don’t share personal information with unsolicited callers: If unsure, hang up immediately and contact the relevant agency directly through their official website or phone number to verify the communication.
- Report suspicious interactions: Inform the appropriate authorities about potential scams to help protect others. Remember, it’s always better to be cautious and independently verify any claims made by someone claiming to be a government representative.
Job Scams
Job scams often target individuals seeking employment, with scammers posing as recruiters or representatives of legitimate-sounding companies. They may offer attractive remote work opportunities with little to no experience required via unsolicited outreach—email, social media, messaging apps, etc.
After carrying out a fake interviews process, they likely request personal information, such as bank account details or Social Security numbers, for “onboarding” purposes or even ask for payment for training materials or equipment as a condition of employment. In many cases, these jobs don’t exist, and the aim is to steal the victim’s information or money.
How to Avoid Job Scams
Job scams are designed to trick people out of their money or personal information by posing as legitimate employment opportunities. To avoid falling victim, keep these tips in mind when evaluating job offers:
- Be wary of unsolicited job offers, especially those that seem too good to be true.
- Research the company using official websites and independent sources.
- Never share sensitive personal or financial information with someone you haven’t fully vetted.
- Know that legitimate employers will not ask you to pay for training or equipment.
- Watch out for vague job descriptions or requests to deposit checks and send the money elsewhere.
- If something feels off about a job offer, trust your instincts and walk away.
Affinity Fraud
Affinity fraud is a scam in which a scammer takes advantage of the trust and shared interests within a specific group, such as a religious, ethnic, or social community, to carry out fraudulent schemes. The perpetrators of affinity fraud often gain credibility by being a part of or targeting a particular group, making it easier to manipulate the trust of individuals within that community. These schemes can involve investment fraud, pyramid schemes, or other financial scams that prey on group members’ shared connections and trust.
Affinity fraud is particularly dangerous because victims are likely to let their guard down due to a sense of shared identity. Exercise caution and conduct thorough research before making financial decisions, even within seemingly trustworthy circles. The ultimate goal of the scammer is to sell something, persuade the victim to make a fraudulent or inappropriate investment, or deceive them into revealing sensitive information. The scammer may be an actual member of the group, even someone the victim knows or likes, or they may simply pretend to be an actual member.
Be careful when someone on the other end of the line requests money or information, regardless of their identity or claims. Suppose they claim to represent a group you support. In that case, it is advisable to use official channels such as their website to ensure your donation reaches the intended recipients and not a scammer.
Scams Targeting Seniors
Unfortunately, seniors are often the group targeted most aggressively by scammers. This means that they need to be extra cautious when answering the phone or browsing the internet and vigilant about keeping their information and money protected. One tactic that scammers can use is to claim to be or represent a loved one who’s in trouble and needs money for an emergency. Seniors and anyone else who receives a call or email like this should always confirm the legitimacy before doing anything.
Dealing with Scammer
When encountering a scammer, prioritize personal safety and immediately cease communication with the individual. Do not provide personal or financial information, such as passwords, credit card details, or Social Security numbers. Block the scammer’s contact and report the incident to the appropriate authorities, such as the local police and relevant online platforms, if the scam occurred digitally. Additionally, notify your bank and other financial institutions if there is a risk of compromised financial information.
If you suspect you have sent money to a scammer, take immediate action. The first step is to cancel any card used and notify your bank or credit union about the theft of your account information. You can also contact an administrator or a helpline for the account. If the scammer has access to sensitive information, like your Social Security number, the FTC website provides useful guidance on what steps you can take next. It is always better to act quickly and take necessary steps to safeguard your personal information to avoid potential harm.
Remember that law enforcement agencies and consumer protection organizations are valuable resources for investigating and addressing fraudulent activities. Scammers always evolve and improve tactics to exploit unsuspecting individuals. To stay protected and informed, visit the Federal Trade Commission’s Federal Trade Commission’s website. There, you can access information about recent scams, as well as helpful tips on how to keep yourself safe.
Disclaimer
While we hope you find this content useful, it is only intended to serve as a starting point. Your next step is to speak with a qualified, licensed professional who can provide advice tailored to your individual circumstances. Nothing in this article, nor in any associated resources, should be construed as financial or legal advice. Furthermore, while we have made good faith efforts to ensure that the information presented was correct as of the date the content was prepared, we are unable to guarantee that it remains accurate today.Neither Banzai nor its sponsoring partners make any warranties or representations as to the accuracy, applicability, completeness, or suitability for any particular purpose of the information contained herein. Banzai and its sponsoring partners expressly disclaim any liability arising from the use or misuse of these materials and, by visiting this site, you agree to release Banzai and its sponsoring partners from any such liability. Do not rely upon the information provided in this content when making decisions regarding financial or legal matters without first consulting with a qualified, licensed professional.
Posted In: Security
Explore All The Ways We Can Help You Grow
-
 Article
Article
11 Important Skills that Every Digital Citizen Should Possess
11 must-have digital citizenship skills. Know how to be responsible online: browsing, cyberbullying, privacy, copyrights, research, and more.
Keep Reading About 11 Important Skills that Every Digital Citizen Should Possess -
 Article
Article
4 Tips for Using Peer-to-Peer Payment Apps
Peer-to-peer payment apps are convenient, but they aren’t without pitfalls. Learn about potential problems before you hit “Send.”
Keep Reading About 4 Tips for Using Peer-to-Peer Payment Apps -
 Article
Article
Scam Alert: The FBI Warns of Reverse Instant Payment Scams
The FBI warns of a new scam that’s affecting many people: reverse instant payment scams. Learn how to keep your money safe.
Keep Reading About Scam Alert: The FBI Warns of Reverse Instant Payment Scams
Lost or Stolen Card?
We’re here to help. If your card has been misplaced or stolen, we’ll act quickly to protect your account. You can report a missing card in the following ways:
Online and Mobile Banking
Log in and follow these three easy steps:
- From the menu, select Tools
- Select Card Manager
- Report your card as Lost or Stolen*
By phone or at a Grow store
Call 800.839.6328 to speak to a team member or let us know in person at any Grow store.Notice: Taking these steps will immediately cancel your card to prevent unauthorized transactions. If you find your card later after reporting it lost or stolen, it cannot be reactivated.
*The selected card will be canceled and removed from Manage Cards when it is reported as lost. Once your new card has been issued, it will be available in Manage Cards. The replacement card will have a new card number. Your replacement card will be sent to the mailing address on your account, and you should receive it within 7 to 10 business days.
How to Find Your Routing & Account Numbers
When you make a payment online, by phone or on a mobile device, you may be asked for our routing number and your checking account number. Credit unions and banks use these numbers to identify accounts and make sure money gets where it’s supposed to be. You’ll also need to provide your routing and checking account numbers for:
- Direct deposits
- Electronic checks
- Military allotments
- Wire transfers
Where to Find Your Routing & Checking Account Numbers
Your personal checks include both our routing number and your account number, as shown on the Grow check example below.
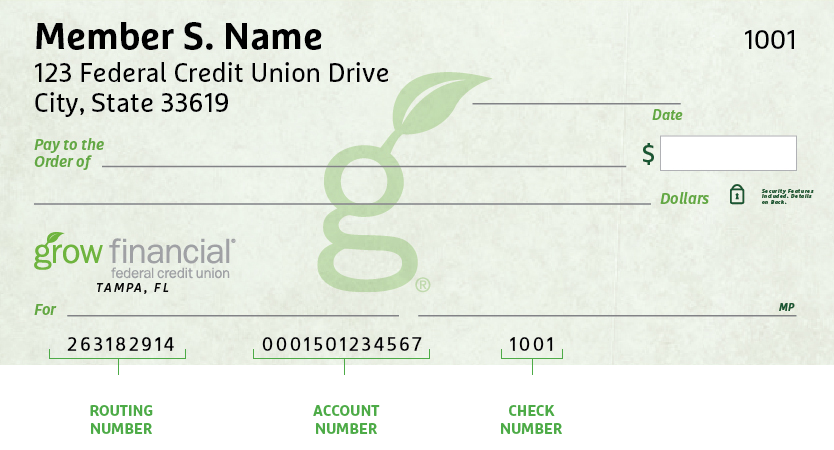
Where to Find Your Checking Account Number in Grow Online and Mobile Banking
If you don’t have a physical check on hand, you can also locate your Checking Account Number for Electronic Transactions in Grow Online and Mobile Banking.*
Here’s how to find it:
- In the Grow Mobile Banking app, select your checking account, then tap Show Details in the top right corner.
- In Grow Online Banking, select your checking account, then click Account Details.
Don’t have a Grow check or Online Banking? No worries.
Visit any Grow store or call us and ask for a Direct Deposit Form. It lists both your routing number and checking account number.
Making a Loan Payment
When it comes to making payments, we try to make it as painless as possible to pay your loan every month. We have several different ways to pay, including convenient online options.
Pay Online
You have two ways to pay online by transferring funds from another bank or credit union.
- Grow Online Banking (Preferred payment method for any loan)
This is the simplest way to pay your loan. You can make one-time payments or set up automatic recurring payments in Grow Online Banking. Once you log in, select “Transfer/Payments” from the menu. If you’re not enrolled in Grow Online Banking yet, you can set up your account in just a few minutes.
Log In
- Debit Card or ACH (Available for auto, personal loans and HELOCs)
Note: ACH and debit card payments are not available for credit cards or most mortgages, except HELOCs.
We accept ACH payments with no additional fees, consumer Mastercard® and Visa® debit cards with a convenience fee of $4.95, or commercial Mastercard® and Visa® debit cards with a convenience fee of 2.95% of the payment amount. To get started with an online ACH or debit card payment, select Pay Now below.
Pay Now
Pay by Mail
You can also pay any Grow loan by check through the mail. Please remember to include your account number and Grow loan number on the check. (For credit card payments, please do not write your 16-digit credit card number on the check, which can cause a delay in processing the payment.)
Address for auto, credit card, personal loan and HELOC payments:
Grow Financial Federal Credit Union
P.O. Box 75466
Chicago, IL 60675-5466Address for personal first or second mortgages and home equity payments:
Grow Financial Federal Credit Union
P.O. Box 11733
Newark, NJ 07101-4733You Are About To Leave GrowFinancial.org
At certain places on this site, there are links to other websites. Grow Financial Federal Credit Union does not endorse, approve, represent, certify or control those external sites. The credit union does not guarantee the accuracy, completeness, efficacy, timeliness or accurate sequencing of the information contained on them. You will not be represented by Grow Financial Federal Credit Union if you enter into a transaction. Privacy and security policies may differ from those practiced by the credit union. Click CONTINUE if you wish to proceed.
